Time once again to upgrade my desktop computer. My current system, an ASUS P67 Sabertooth motherboard (P67 Chipset/Socket 1155), Intel Core i7-2600K (Sandy Bridge) processor, AMD Radeon HD 6950 GPU, and 8 GB of DDR3-1600 G.Skill RAM, served me well, but I wanted to move on to Intel’s “Ivy Bridge” architecture. This post will document my upgrade, starting with the parts I selected and why; the assembly of the system and the challenges I encountered; and finally, a few thoughts on overclocking the upgraded system.
The Parts
In keeping with previous builds, my goal was to use the best quality components I could find for a reasonable price, and build a good, fast, and reliable machine for PC gaming. In other words, build a machine that’s represents a good value.
The Case – I looked for a mid-tower case that featured good air flow and plenty of room for wiring. The NZXT Tempest case I used for my Sandy Bridge build had served me well, but turned out to be a a bit constraining when it came to routing wiring and keeping the inside of the case looking neat. This time I settled on the Corsair Graphite Series 600T. The 600T is a mid-tower in height, but nearly 11 inches wide. Pre-cut holes with rubber grommets in the motherboard tray combined with plenty of room behind it allowed for clean, uncluttered cable routing; and the dual 200mm fans located at the top of the case assisted in providing very good cooling.
The Power Supply – I decided to go with the Corsair TX750 V2. Corsair’s power supplies are quality products, featuring a single dedicated, single +12V rail for maximum and efficient power distribution and they’re sensibly priced. The unit is 80 PLUS Bronze certified (> 80% efficient) and quiet.
The Processor – After doing a little research and giving it much consideration, I chose the Intel Core i7-3770k processor with a 3.5 GHz base clock frequency, 3.9 GHz maximum default “turbo” frequency, and 8 MB of L3 cache and hyper-threading. Besides the featuring the highest clock frequency among the mid-range Ivy Bridge socket 1155 desktop processors, the “K” suffix means the “turbo mode” multipliers are fully unlocked, giving this processor a lot of overclocking potential.
The Motherboard – The ASUS Sabertooth P67 board meet my needs so well for my Sandy Bridge build that I decided to turn to them once again, selecting the Sabertooth Z77 board for this build.
The Heatsink – After doing a bit a research to make sure it would clear the surrounding components on the motherboard, including the RAM, I chose the Cooler Master Hyper 212 Plus. To improve its already very good cooling capabilities, I purchased an additional Cooler Master 120 mm fan to match the fan the product shipped with and then set it up in a push/pull configuration. This configuration combined with the Corsair case provides very good overall processor cooling. Finally, to ensure that both fans would rotate at reasonably the same speed, I used a PWM splitter from Rosewill to power and control both fans from the processor fan header.
The RAM – I was looking to upgrade to 16 GB of RAM this time around, with timings as low as possible. A factor that I was again glad I considered ahead of time was whether the RAM would fit under the processor’s fan/heatsink due to the close proximity of the RAM slots to processor. I ended up eliminated a couple of products (Corsair’s “Dominator” as an example) because they were simply too tall to fit. Finally I ended up selecting G.Skill’s RipjawsX DDR3-1866 16 GB kit (4 * 4GB), which runs at 1.5v with timings specified at 9-10-9-28.
The Graphics – I with AMD again. After doing looking at some online comparisons, choosing Gigabyte’s version of AMD’s Radeon HD 7870, the GV-R787OC-2GD. At ~$360, it provided the best performance for the money. Indeed, given my 24-inch Dell monitor’s 1920 * 1200 resolution, this GPU should easily handle nearly any game I throw at it.
The Hard Drives – With this build I decided to step up the size and performance of the SSD drive and selected a 2.5-inch OCZ Vertex 4 120 GB SATA 6 Gb/s drive. This will serve as my system drive, containing the operating system and a few of my most used applications and games, while a Western Digital Caviar Black 1TB 7200 RPM 64MB cache SATA 3.0 drive will hold the bulk of my non-OS data.
The Optical Drive – Yup, still use one of these :). In this case, the venerable ASUS DRW-24B1ST.
The Operating System – Not much of a surprise here, I went with Windows 7 Pro 64-bit. The Home Premium version doesn’t support Remote Desktop connections from another computer, a feature I use daily, and this of course is my gaming rig, leaving a Linux out of the hunt (for now). Besides, I get my *nix on using my laptop, which is setup to dual boot windows and several Linux distros, as well as various other machines I administer.
The Build
Time to put those parts to some use. I typically build my systems outside of the case first, then when I’m sure everything is running well, I’ll place the components in the case and dress up the wiring (See Figure 1).
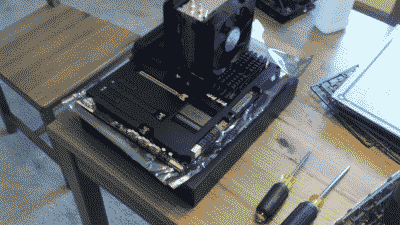
Figure 1
The SATA 3.0 and SATA 6.0 ports on the ASUS Z77 are mounted horizontally on the board, making it easier to connect/disconnect disk drives with graphics cards in place. I connected the 120 GB OCZ Vertex 4 drive to the SATA 6.0 GB port 1, and the 1TB WD Caviar Black drive on the SATA 6.0 port 2. These are the Brown SATA ports on the ASUS Sabertooth Z77 motherboard.
When mounting the Cooler Master Hyper 212 Plus, I was able to achieve the lowest processor temperatures by applying two thin lines of thermal compound, in this case, Artic’s Silver 5, to the two center mounting base partitions heat sync (See Figure 2). My idle temperatures are hovering around ~28C when measured in UEFI and approximately the same when measured from within Windows using Real Temp.

Figure 2
The Sabertooth motherboards are equipped with what ASUS calls “TUF Thermal Armor,” a marketing term that ASUS uses to denote what is essentially a large heatsink that encompasses nearly the entire motherboard. The idea behind this unorthodox design is to conduct the hot air generated by cards and components out of the case through special air flow channels, thus reducing the overall temperature of the motherboard, and by extension the inside the the PC case. To do this effectively, however, ASUS recommends that system builders use a processor fan that directs air downward into the motherboard. Unfortunately, like most processor fan/heatsink products made for the PC enthusiasts market, the Cooler Master Hyper 212 Plus is mounted vertically, directing air out the back of the case, not downward towards the motherboard’s components. In anticipation of the situation, ASUS provides a small 50mm fan and a spot on the motherboard to mount it in order to improve the air flow through the TUF Thermal Armor.
After successfully assembling the components, and firing up the system without issue, I proceeded to update the Z77’s UEFI firmware to the latest version. Fortunately ASUS makes this task incredibly easy, offering a number of ways to perform the update, including directly from Windows. I chose to perform the update directly from within the UEFI. First, I downloaded the latest firmware code to a USB flash drive, then inserted the drive into a USB 2.0 port. I entered the “Advanced Mode” of UEFI, navigated to the “Tool” menu, and selected “ASUS EZ Flash Utility.” I highlighted the USB drive containing the ROM file and selected “Enter” to proceed with the UEFI firmware update.
Before installing the operating system on the OCZ Vertex 4 drive, I decided to do a little research on what it would take to update its firmware from version 1.3 to 1.4, which I understood from the OCZ forums would yield better performance from the drive. I’m glad I did, for as it turned out, the version 1.4 firmware update is destructive; meaning if I had gone through process of installing the OS, the update would have simply deleted it. Therefore, performing an update required attaching the drive to another Windows-based machine.
Then I encountered another challenge. The OCZ firmware update tool would indicate that the firmware had updated successfully to version 1.4 and to reboot; however, the tool would then continue to indicate the firmware was version 1.3. The work-around for this problem was odd but it worked. First, I booted the machine. Then I unplugged the power cable from the back of the drive, waited a couple of minutes, and plugged the power back in. Then I proceeded with the update. Once updated, I rebooted and the update tool reported the firmware had indeed successfully updated to version 1.4. It appears the effort was worth it however. A quick look at the performance of the drive using the ATTO Disk Benchmark indicated sequential reads/writes of 476 MB/384MB respectively using 128 KB transfer size.
After successfully installing Windows 7 and all of the device drivers installed, Window’s Device Manager still indicated that a driver for the “PCI Simple Communications Controller” was still missing (The dreaded yellow exclamation mark). It turned out to be a simple fix, but one I always seem to forget to do – download and install Intel’s Management Engine Interface utility from ASUS.
Finally, to improve the reliability of the Z77 Sabertooth’s Ethernet interface I downloaded and installed Intel’s driver for the 82579 Ethernet network interface controller on the Z77. Then, I entered the UEFI’s Advanced mode, navigated to Advanced -> APM and enabled “Power On By PCI” to activate the board’s Wake-on-LAN feature.
With these issues out of way I continued on, updating Windows, adding applications, tweaking options and generally letting the system burn-in for a bit. Then it was time to move on to overclocking the system.
The Overclock
By default the Core i7-3770K runs at 3.5GHz but can turbo boost itself to 3.9GHz if all four cores are not being utilized, and assuming it is operating within what Intel feels are acceptable power and temperature limits. However, Like all of Intel’s “K”suffix processors, the i7-3770K is multiplier-unlocked – this time up to 63x compared to 57x on the Sandy Bridge Core i7-2770K. Therefore, assuming the BCLK bus is running at its default of 100MHz, you could theoretical achieve a maximum CPU speed of the 6.3GHz simply by adjusting the multiplier, assuming of course that you had the necessary cooling solution.
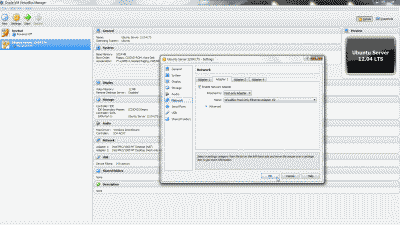
For this build I took a much more conservative route. Not unlike most of the “enthusiasts” motherboards on the market today, the Sabertooth Z77 offers a method to automatically overclock your system, dispensing with the need in most cases to independently adjust BCLK, multiplier, memory, and voltage settings. In fact, the Z67 offers two methods: one is available by navigating to the in the UEFI’s “EZ Mode” settings and selecting the “Performance” option. The other is available by navigating to Advanced Mode -> Ai Tweaker and selecting “OC Tuner.” I decided to give the EZ Mode Performance option a go and was quite happy with the results (See Figure 3).
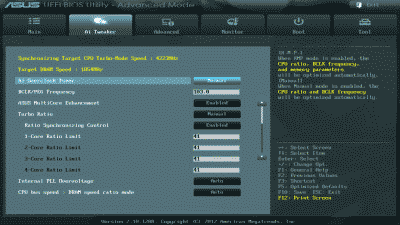
Figure 3
The BCLK was increased to 103 MHz and the Turbo Mode multiplier for all four cores to 41. This resulted in an overall processor speed of ~4.2 GHz when running in Turbo Mode. My DDR3-1866 memory essentially remained unchanged. Like I said, conservative. But fast enough for the time being, with plenty of headroom to make further increases in the future if desired.
Next, I adjusted my memory timings to the 9-10-9-28 and ran Memtest86+ for a couple of passes to ensure those timings and the memory in general was sound. Then I ran the 64-bit version of Prime 95 using the “Large in-place FFT” setting for ~24 hours to ensure that the system stability and maximum processor core temperatures were kept in check. I should note that ambient room temperature during the Prime 95 testing was ~21 C. The tests resulted in no errors and the maximum processor core temperatures peaked at ~86 C but on average were ~80C. (See Figure 4).
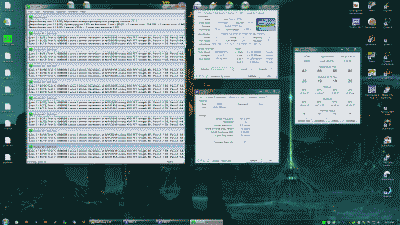
Figure 4
Conclusion
I couldn’t be more pleased with this build. Intel’s Core i7-3770K processor and ASUS’s Sabertooth Z777 motherboard is a solid mid-range combination. Since its completion, the system has been 100% stable.