(20180108 – The steps in this post were amended to address changes in the Amazon AWS service — iceflatline)
FreeBSD is an free and open source advanced computer operating system used to power modern servers, desktops and embedded platforms.
Amazon Elastic Compute Cloud (“EC2”) provides resizable computing capacity in the Amazon Web Services (“AWS”) cloud. Amazon EC2 can be used to launch as many or as few virtual servers as you need, configure security and networking, and manage storage. An Amazon Machine Image (AMI) is a template that contains a software configuration (for example, an operating system, an application server, and applications). From an AMI, you launch an instance; virtual servers that can run applications. Instances feature varying combinations of CPU, memory, storage, and networking capacity, and give you the flexibility to choose the appropriate mix of resources for your applications.
This post describes how to create and configure a FreeBSD instance in Amazon EC2. Then goes on to explain how to connect to the new instance using SSH from a machine running a BSD, Linux or Windows operating system.
The steps discussed in this post assume you have an active AWS account. If you do not, you can sign up for one at Amazon Web Services.
Let’s get started…
Create and Configure the FreeBSD Instance
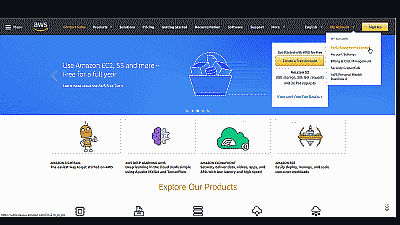
Fire up your web browser and navigate to Amazon Web Services. Login to the AWS Management Console by selecting “AWS Managment Console” from among the options in the drop down list under “My Account” (See Figure 1).
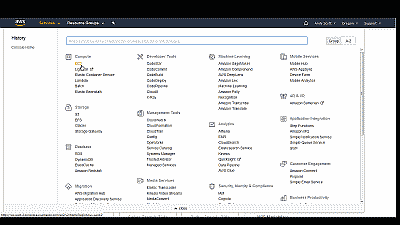
Once you’ve successfully logged in, select “EC2″ from among the options listed under the “Services” section (See Figure 2).
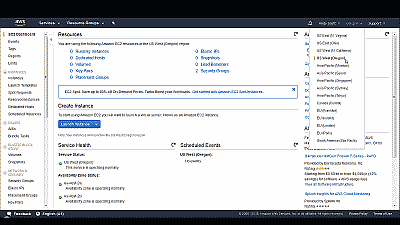
Next you’ll choose the Amazon EC2 “region” under which the FreeBSD instance will be created. In this example we’ll select the US West (Oregon) region (See Figure 3).
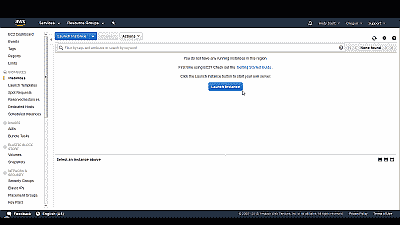
Now select “Instances” from among the options under the “Instances” category on the left side of the page. If this is the first time you’ve created an instance in this Amazon EC2 region you’ll be greeted with a message indicating “you do not have any running instances in this region” and a button to launch one (See Figure 4).
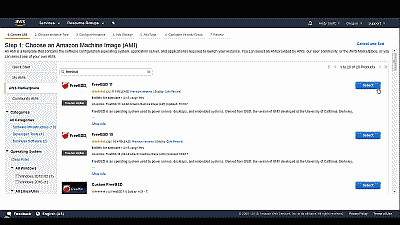
Select “Launch Instance” and you’ll be greeted with Amazon’s quick start guide for creating a new AMI. Select “AWS Marketplace” from among the choices on the left side of the web page where you will be offered the ability to search for and select an AMI. Simply search for “freebsd” and you will presented with several FreeBSD image options (See Figure 5).
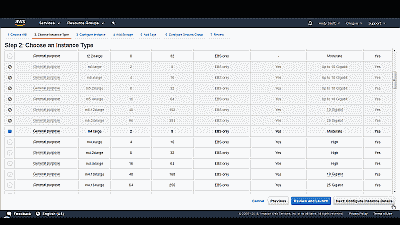
In this example we’ll select the “FreeBSD 11” AMI, where we’ll be presented with some product details, including instance pricing. Select “Continue” where you’ll be asked to choose an instance type. Amazon EC2 provides several instance types optimized to fit different use cases. In this example we’ll use the recommended m4.large instance. (See Figure 6).
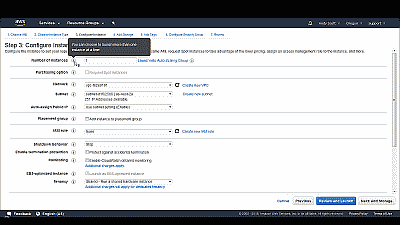
Select “Next: Configure Instance Details” where you will be presented with a list of default options that can be modified, if desired, to better suite your needs. Hovering your mouse over the “i” icon near an option will describe its purpose in greater detail. One option that may prove helpful is the termination protection. Enabling this option will prevent the instance from being accidentally “terminated” (i.e., deleted). If enabled, you will not be able to delete the instance through the AWS Management Console until this option is once again disabled. For our example, however, we’ll simply retain the default options (See Figure 7).
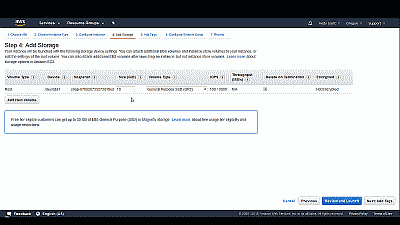
Now select “Next: Add Storage” where you can adjust the size of the default or “root” Elastic Block Store (“EBS”) volume. You can also attach additional EBS volumes to your instance, or edit the settings of the root volume. You can also choose to delete the volume should you decide to terminate the instance. For our example, we’ll retain the 10GB root EBS volume and all default settings (See Figure 8).
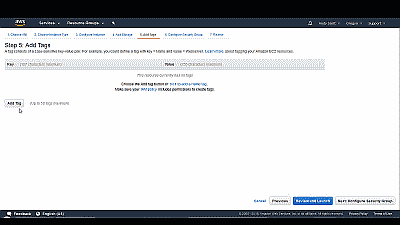
After configuring storage, select “Next: Add Tags” where you be given the option of creating a “Tag” for your instance (See Figure 9). Tags enable you to categorize your AWS resources in different ways, for example, by purpose, owner, or environment. Each tag consists of a key and a value, both of which you can define. Uniquely tagging instances can be beneficial, particularly if you plan on creating many of them. Again, this is an optional step, and since we’re creating a single instance, we’ll forgo tagging and move on to the next step: Configure Security Group.
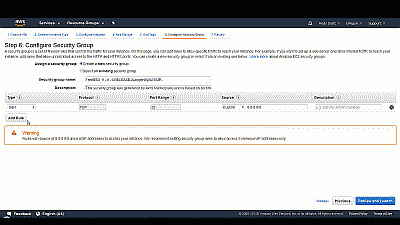
A security group is a set of firewall rules that control the traffic for your instance. For example, if you want to set up a web server and allow traffic to reach your instance, you would add rules that permit unrestricted access to HTTP and HTTPS ports. You can create a new security group or select from an existing one. In this example, we would simply like to connect to the new FreeBSD instance using a secure shell (SSH) so there is no need to create a new rule as one already exists for SSH by default. However, you may wish to filter incoming SSH connections to your FreeBSD instance. If you’d like to connect from any network, then simply retain the select “custom” from among the options in the drop down list under “Source”, else you can limit incoming connections to the IP your currently using or to a custom IP address or IP subnet. For this example, we’ll allow incoming SSH connections on port 22 from anywhere (See Figure 10).
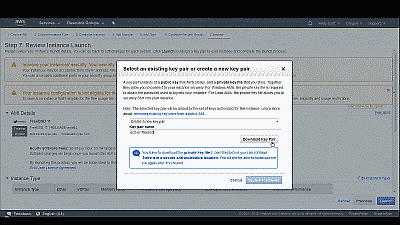
When complete, select “Review and Launch” where you’ll be given one last opportunity to modify your settings. If everything checks out select “Launch” where a pop up screen will provide the opportunity to select an existing key pair or create a new key pair. A key pair consists of a OpenSSL public key, which Amazon AWS retains and copies to your instance, and a private key that you download and retain. Together, they allow you to connect to your FreeBSD instance securely using SSH. If this this is first time you’ve created an instance you’ll likely not have an existing key pair from which to chose. If this is the case, select “Create a new key pair” from among the options in the drop down list and enter a name for your new key pair. In this example we’ll use the name “ec2-or-freebsd.” Now select “Download Key Pair” and save the file in a secure and accessible location (See Figure 11).
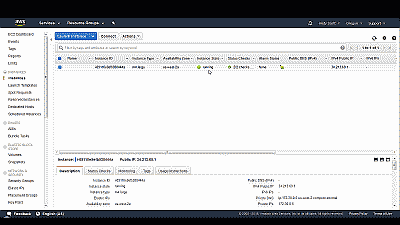
Next, select “Launch Instances”, followed by “View Instances” and you’ll be taken to a page showing your FreeBSD instance launching. After a minute or two, the “Instance State” will change from “pending” to “running” (See Figure 12). You can stop your instance by selecting “Stop” from among the options in the drop down list under “Actions” located at the top of the page.
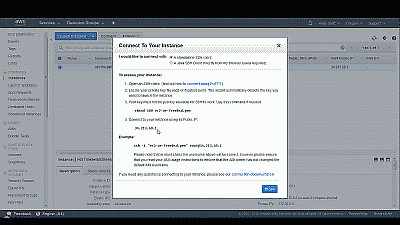
Finally, let’s get the public IP address of our FreeBSD instance. Select “Connect” at the top of the instance page and make a note of the public IP address assigned to your instance (See Figure 13). Note that the instance will be assigned a new public IP address if you stop it and restart it. If you want to avoid this situation then consider using an Elastic IP address. If you simply reboot the instance from within the operating system it will retain the same public IP addresses.
Connect to the instance from Windows
Now that we have our new FreeBSD instance up and running under Amazon EC2 let’s turn our attention to connecting to it using SSH under Windows. Since Windows doesn’t typically support SSH, we’ll need an SSH client. There are many out there to choose from, but the one we’ll use in this example is PuTTY, a free implementation of Telnet and SSH for Windows and Linux/BSD platforms.
PuTTY does not natively support the private key format *.pem generated by Amazon EC2, so we’ll also need a way to convert this key file to a key format that the PuTTY application can use. For this we’ll use PuTTYgen, a free key generation utility, which can convert keys to *.ppk, the file format required by PuTTY. You can download standalone versions of PuTTY and PuTTYgen, or simply download the Windows installer version of PuTTY, which will also install PuTTYgen, as well as Pageant, an SSH authentication agent for PuTTY.
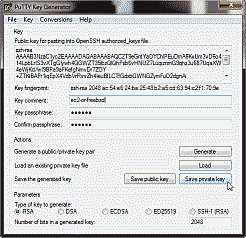
Fire up PuTTYgen and select “Load”. Navigate to where you downloaded the ec2-or-freebsd.pem file and select “Open” (Note: you may have to change the search filter from “PuTTY Private Key Files (*.PPK)” to “All Files (*.*)” in order to readily locate the file). Once ec2-or-freebsd.pem has been successfully loaded into PuTTYgen, you can modify the “Key comment” field if desired, as well as add a passphrase to protect your private key. Electing not to means that anyone gaining access to your private key will also quite easily be able to access your FreeBSD instance. Once complete select “Save private key” and select a name (for this example, we’ll use the same name: ec2-or-freebsd) and a location to save the new key file (See Figure 14).
Exit out of PuTTYgen and fire up PuTTY. Navigate to Connection->SSH->Auth. Under Authentication parameters select the Browse button and select the ec2-or-freebsd.ppk file you saved in the previous step. Navigate back up to Session. You’ll connect as “ec2-user” so prepend this user name to the public IP address assigned to your instance so that the entire field looks like this: “ec2-user@
Now select “Open” and the PuTTY client will connect to your FreeBSD instance. If this is the first time you’ve connected to it, you’ll receive a warning concerning the authenticity of the host you’re trying to reach. If you’re sure this is the correct instance and you want to continue connecting, select “Yes” to add the key to PuTTY’s cache and carry on connecting. If you want to carry on connecting just once, without adding the key to the cache, select “No”. You’ll be asked to provide the passphrase (if you created one) for your private key and you’ll be connected to the instance.
Connect from FreeBSD or Linux
Connecting to your FreeBSD EC2 instance via SSH is significantly easier in FreeBSD or Linux. Start by checking to see if the .ssh directory exists in your home directory. If it does not, create it and set it’s permissions appropriately:
|
1 2 |
mkdir ~/.ssh chmod 700 ~/.ssh |
Now move the ec2-or-freebsd.pem file you downloaded to ~/.ssh and modify its permissions appropriately:
|
1 |
chmod 600 ~/.ssh/ec2-or-freebsd.pem |
As an optional security step you can add a passphrase to your key:
|
1 |
openssl rsa -in ec2-or-freebsd.pem -des3 -out ec2-or-freebsd.pem |
Now let’s connect to our FreeBSD instance:
|
1 |
ssh -i ~/.ssh/ec2-or-freebsd.pem ec2-user@<your-instance-public-IP-address> |
If you chose a different port number than the default when setting up the instance’s security group, then you’ll need to specify that on the command line as well:
|
1 |
ssh -p <your-port-number> -i ~/.ssh/ec2-or-freebsd.pem ec2-user@<your-instance-public-IP-address> |
If this is the first time you’ve connected to it, you’ll receive a warning concerning the authenticity of the host you’re trying to reach. If you’re sure this is the correct instance and you want to continue connecting type “yes” at the prompt. The public key of your FreeBSD EC2 instance will be added to ~/.ssh/known_hosts and you will be connected.
Conclusion
Well, that’s it. With a little effort you can easily create, configure and connect to your own FreeBSD instance in Amazon EC2. Now that you know that your *.ppk and/or *.pem private key works, you should back it up to offline media such as a flash drive or CD and keep it someplace secure. I also strongly recommend that you create a password for the user root in your FreeBSD instance(s).
Issues to note
Amazon does not provide a easy way to verify the key fingerprint – the one listed in the EC2 Management Console. I did manage to find this rather obscure command that will work from FreeBSD and Linux, but I have yet to find an easy way to perform this task under Windows, outside of installing and setting up the the Amazon EC2 command line interface tools.
|
1 |
openssl pkcs8 -in ec2-or-freebsd.pem -nocrypt -topk8 -outform DER | openssl sha1 -c |
References
http://aws.amazon.com/documentation/ec2/
http://www.daemonology.net/blog/2017-10-21-FreeBSD-EC2-community-vs-marketplace-AMIs.html
Thanks IceFlatLine for the detailed information,
Is it possible to be “root” on this FreeBSD system? (sudo is not available)
Abhi, like any FreeBSD system you should be able to become root using the su command.